The perks of IT Compliance with hybrid cloud, DevOps and containers
Current Scenario-
Business units in Hybrid Cloud demands the capacity to release new software designs and highlights quickly. To improve release lifecycles, a line of business groups have implemented open-source tools for setup, arrangement, and release automation.
What is a Hybrid Cloud?
Hybrid cloud is a cloud computing platform that uses a blend of on-premises, private cloud and the third party, public cloud administrations with organization between the two platforms. The hybrid cloud provides organizations with more noteworthy adaptability and more information arrangement alternatives.

Source- virtualizationpractice
What is DevOps?
DevOps is the combination of social concepts, practices, and strategies that forms an association’s ability to convey applications and services at high promptness: advancing and enhancing products at a quicker pace than associations utilizing conventional programming improvement and organization management processes.
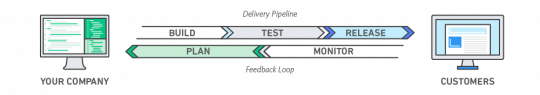
Source- AWS
What are Containers?
Containers are a process of operating framework virtualization that enable you to run an application and its conditions in asset disengaged forms. Virtual Containers can help guarantee that applications send rapidly, dependable, and reliably irrespective of arrangement condition.

Source- cloud.google
The benefits of IT Compliance with hybrid cloud
As technology progresses and new competencies are presented architects must also factor in the expanding number of controls to which their answers must follow. In the event that the business does not meet the required consistency values, the expenses to the business could be extensive. Some the highlights associations should search for in arrangements so as to effectively build a hybrid IT situation.
Secure Approach-
Safeguarding the pathways among devices and information includes securing the passage between them. Connecting operator validation and device compliance will ensure the reliability of the enterprise information and the security of the channel itself.

Comments
Post a Comment